What is Petya ransomware?
Petya encrypts certain files on your computer, then demands a ransom payment in exchange for a decryption key. But while many other strains of ransomware focus on personal files like documents or photos, Petya can lock up your entire hard drive, preventing your computer from booting up at all.
Where does Petya ransomware come from?
Petya isn’t a single instance of ransomware so much as a family of related malware. Petya first appeared in early 2016, spread via malicious email attachments. When downloaded and opened, the attachment would unleash the malware onto the victim’s computer.
After a relatively unremarkable start, Petya exploded into the global cybersecurity conversation with a renewed attack in 2017. Dubbed “NotPetya,” the new variant tore through organizations in Ukraine, including the National Bank of Ukraine, before spreading across Europe and the US. In total, the 2017 NotPetya attack caused over $10 billion in damages.
Fun fact: Petya’s name is a reference to the James Bond film GoldenEye. A Twitter account allegedly belonging to one of Petya’s authors featured two of the film’s antagonists in its name and avatar.
How does Petya work?
Petya ransomware encrypts your computer’s master file table (MFT). The MFT is your computer’s quick-reference guide for every single file on your drive. Without access to the MFT, your computer can’t find any of its files, and so it can’t even boot up — much less function normally.
After the victim unwittingly installs Petya onto a Windows computer, it infects the master boot record (MBR). The MBR is the part of a computer’s programming that is responsible for loading its operating system every time the computer is turned on. Once inside the MBR, Petya forces the computer to restart, then begins encrypting the MFT while displaying its ransom note.
At this point, the computer is unable to access anything on its hard drive, even including its own operating system.
For a thorough exploration into exactly how Petya works, along with the related ransomware Mischa, check out this detailed analysis performed by our Avast Threat Intelligence Team in response to the initial 2016 attacks.
How to detect Petya ransomware
Petya originally relied on user gullibility in order to gain access to computers. You’d have to open the malicious email, download the attachment, open the attachment, and then also agree to give it administrative-level permission to alter the Windows operating system. Only after the completion of this process was Petya able to begin encrypting the MFT.
At this point, the victim’s computer rebooted, then displayed Petya’s ransom message.
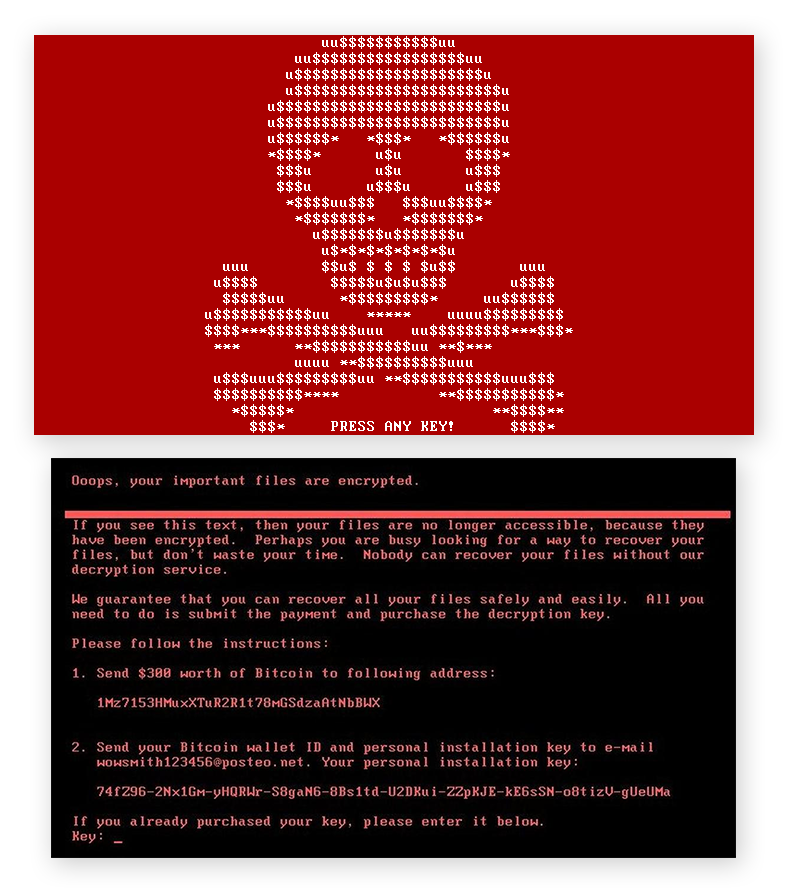
After a few months, Petya began to arrive bundled with a secondary and more conventional ransomware program dubbed “Mischa”. If a victim refused to grant Petya the administrative privileges it needed to encrypt the MFT, Mischa would step in and encrypt the victim’s files — executable programs in addition to the documents, photos, and videos usually targeted by ransomware.
Anti-ransomware software will scan for any signs of known ransomware, including Petya. You’ll be able to detect Petya in time to avoid opening the malicious attachments.
What’s the difference between Petya and NotPetya?
NotPetya takes advantage of the EternalBlue Windows exploit, also used several months earlier by fellow ransomware strain WannaCry. EternalBlue allows malware like NotPetya to spread rapidly on its own within a network, potentially infecting an entire organization within hours.
The 2017 attack targeted massive corporations including banks, energy providers, and shipping conglomerates. In addition to the new infection vector, NotPetya had one additional, crucial difference from its 2016 counterpart: there is no cure. NotPetya permanently encrypts any computer it touches, and due to the way this encryption occurs, it’s impossible to undo even if you pay the ransom. It’s a type of malware known as a wiper, just masquerading as ransomware.
This change has led many cybersecurity experts to conclude that the 2017 NotPetya attack wasn’t a ransom attempt so much as a straightforward cyberattack intended to disrupt and damage targeted systems in Ukraine. It’s even been theorized that the ransomware disguise was intended to frame the attack as a criminal enterprise, potentially hiding origins as a state-sponsored cyberwar foray.
Since the EternalBlue vulnerability that NotPetya used has been patched, it’s very unlikely that you’ll ever encounter this particular strain of malware — so long as you’ve been updating your software, as you always should.
What’s the difference between WannaCry and Petya?
WannaCry and Petya both caused more than their fair shares of chaos during the late spring and early summer of 2017. Though they relied on the same (now-obsolete) vulnerability to infect users, what happened next would depend on which strain of ransomware was involved.
While the Petya/NotPetya attack was later shown to be less ransom-based and more about pure carnage, WannaCry operated along standard ransomware protocols, leaving the MBR and MFT untouched. Additionally, Petya proved to be much more adept at resisting containment attempts. It could still infect computers running patched software and could also spread through other means outside the EternalBlue exploit.
There have also been numerous other instances of ransomware, such as Locky, Cerber, and CryptoLocker.
How to remove Petya ransomware?
Because ransomware encrypts your files, removing it solves only half the problem. Once the ransomware is gone, you’ve still got a bunch of encrypted files to deal with.
You can remove most conventional strains of ransomware easily with your preferred anti-malware tool. Since the ransomware only encrypts individual files and folders, you’ve still got access to your operating system and all the programs on it. You can quickly activate or install a cybersecurity program to remove ransomware on your PC (or Mac) and let it go to work.
A Petya infection isn’t so simple. With the MFT in Petya’s stranglehold, your computer can’t load its OS, which means that you won’t be able to access your cybersecurity software. Instead, you have two options:
-
There’s a bit of a delay between the moment Petya arrives on your computer and when it forces your computer to reboot. If you can power your computer down before Petya completes the reboot, you may be able to prevent it from encrypting your MFT.
-
If you see the red skull & crossbones screen shown above, it’s game over. You’ll have no choice but to take your computer offline, reformat its hard drive, then restore your files from the backup that you’ve hopefully created.
Never succumb to the temptation to pay the ransom. Remember that some variants of Petya aren’t decryptable, even by the cybercriminals themselves. In these cases, Petya is a one-way street, and there’s no going back. Other variants have been cracked, and you may be able to find decryptors online. If you’re infected with Petya, consult with a cybersecurity expert to identify the type plaguing your computer.
Even in cases where the encryption can be reversed, paying the ransom isn’t a guarantee that you’ll regain access to your files. The cybercriminal may just as well abscond with your payment. Plus, when you pay up, you’re only validating their use of ransomware as a lucrative cybercrime technique. By refusing to pay, you can discourage cybercriminals from using ransomware against others.
How to prevent Petya ransomware?
Rather than face the consequences of a Petya infection, do yourself a solid and focus on prevention with these anti-ransomware best practices:
-
 Be stingy with admin privileges. Never give any software administrative privileges unless you are absolutely sure that it’s legitimate and necessary.
Be stingy with admin privileges. Never give any software administrative privileges unless you are absolutely sure that it’s legitimate and necessary.
-
 Be an email skeptic. Always err on the side of caution when it comes to links and attachments in emails. If you don’t download the attachment or click the link in the sketchy email, you won’t get the ransomware.
Be an email skeptic. Always err on the side of caution when it comes to links and attachments in emails. If you don’t download the attachment or click the link in the sketchy email, you won’t get the ransomware.
-
 Always update your software. Malware exploits software vulnerabilities, and as these are discovered, companies are quick to patch them with updated versions. Install patches and updates as soon as you receive them.
Always update your software. Malware exploits software vulnerabilities, and as these are discovered, companies are quick to patch them with updated versions. Install patches and updates as soon as you receive them.
-
 Use an anti-malware tool. Reliable antivirus software is your best defense in the fight against Petya and other malware. It’ll detect and block malware before it has a chance to infect your machine.
Use an anti-malware tool. Reliable antivirus software is your best defense in the fight against Petya and other malware. It’ll detect and block malware before it has a chance to infect your machine.
-
 Don’t click internet ads. Malicious ads, especially pop-ups, are a common source for malware infections. No matter what it says, leave the ad alone. This counts double when visiting unfamiliar websites.
Don’t click internet ads. Malicious ads, especially pop-ups, are a common source for malware infections. No matter what it says, leave the ad alone. This counts double when visiting unfamiliar websites.
-
 Regularly backup your files. A ransomware infection won’t mean a thing if you’ve got a fresh backup of all your important files. Cloud services and physical drives are both viable backup choices, and so whichever you prefer, use it often. When you finish backing up your files, disconnect from the backup to prevent malware from reaching it.
Regularly backup your files. A ransomware infection won’t mean a thing if you’ve got a fresh backup of all your important files. Cloud services and physical drives are both viable backup choices, and so whichever you prefer, use it often. When you finish backing up your files, disconnect from the backup to prevent malware from reaching it.
Defend against ransomware with Avast
At Avast, we’re on the frontlines of the fight against malware. Avast One is constantly updated to identify, detect, and block the newest types of malware as they emerge. It’ll also alert you to any other security weak points on your device or network, including outdated software or unprotected Wi-Fi, protecting you from cyberattacks on all sides.
It’s just one of the many reasons why over 400 million people around the world trust Avast with their privacy and security.