Locky attacks victims by encrypting their files — rendering them both inaccessible and unusable — and then requiring a payment in exchange for restoring things to normal. The cybercriminals promise to give users a Locky ransomware decryption key that only they possess, thus compelling victims to pay the ransom.
Where does Locky come from?
Locky relies on social engineering techniques to get onto victims’ computers, with email as its transmission vector of choice. This nasty bit of ransomware first emerged in 2016 and spread quickly throughout many regions of the world, including North America, Europe, and Asia. One of the first major attacks targeted a hospital in Los Angeles, forcing them to hand over a $17,000 ransom payment. A sustained campaign against other healthcare institutions continued throughout the year. Since then, there haven’t been any other significant Locky attacks.

By analyzing some of Locky’s components, the Avast Threat Intelligence Team was able to uncover evidence linking the new ransomware to a notorious hacking collective known as Dridex.
How can I detect Locky ransomware?
Targets receive a fraudulent email containing a malicious attachment that delivers Locky onto their computer. These emails are often disguised as payment invoices, with subjects such as “Upcoming Payment – 1 Month Notice”. No one likes owing money, and this feeling is what motivates victims to open the emails.
If you’re running an active anti-ransomware tool, it will handle the detecting for you. Strong protection from a reputable provider is your best defense against Locky and other ransomware.
How does Locky work?
Once you open the email, you’ll be directed to download an attachment, often a Microsoft Word document. The contents of the document are intentional gibberish, and here’s where the social engineering comes into play:
After you open the attached document, it’ll prompt you to enable your Word macros so that its contents can be displayed properly. A macro is somewhat like a shortcut that performs some sort of automated function. Going along with the prompt and enabling your macros also activates a malicious script that installs the latest version of Locky on your computer.
As soon as this happens, your files are locked up tight. One reason Locky is so dangerous is because of the variety of files that it can encrypt. In addition to Microsoft Office files and videos, Locky can even scramble your computer’s source code, which makes your computer unusable. Your files will be renamed and have their extensions changed to new ones, which may include .aesir, .odin, .osiris, .thor and .locky itself.
At this point, Locky will show you its ransom note, localized to your area. You’ll be asked to install the Tor browser and transfer a fee in Bitcoin (BTC) in exchange for the decryption key. Typical ransom demands range from 0.5 to 1.0 Bitcoin (BTC), roughly $4,000 to $8,000 as of November 2019. If you have a BTC wallet on your computer, Locky can even encrypt that!
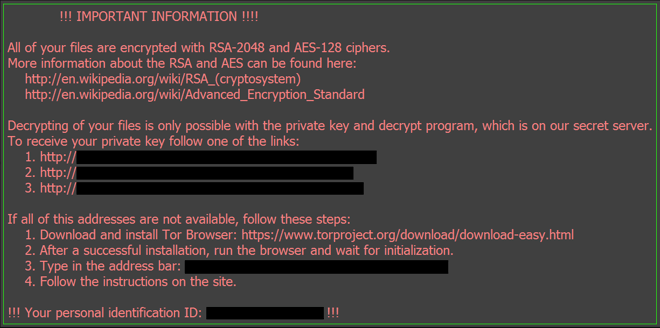
How to remove Locky ransomware
If you’re facing a Locky infection, an anti-malware program will be able to remove it along with any associated malware from your computer. Simply fire up your antivirus software and let it do its job.
Note that removing ransomware will not decrypt and restore your files. There is currently no known cure for Locky’s encryption methods, and so once it gets ahold of your files, they are gone. Some strains of ransomware can be countered using the Shadow Copy files created by the Windows Volume Snapshot Service or with Avast's own free decryption keys, but unfortunately Locky manages to elude all possible fixes.
By now, you might be coming to the conclusion that you can get your files back if you pay the ransom. This is not true. There is no guarantee whatsoever that the cybercriminals behind the Locky attacks will follow through on their promise. By giving into their ransom demands, you’re confirming that their methods are effective and encouraging them to use them against additional victims. Lastly, your ransom money will likely be used for future criminal activities.
The only reliable way to recover your files from a Locky infection is to restore them from an uninfected backup — that’s why it’s so crucial to stay one step ahead of the hackers and perform regular backups of your computer.
How to prevent Locky ransomware
Ransomware is one of the most difficult types of malware to deal with once you’ve been infected, so prevention is always going to be your best defense strategy. Practice the following tips to keep your device safe from Locky and other ransomware:
-
Regularly back up your files: Whether you’re using a cloud service or an external drive, back your files up from time to time. If you’ve opted for an external storage device, disconnect it as soon as your backup is complete. Locky can spread to any connected devices as well as any networks it can access, so be sure to put your backup drive away.
-
Don’t download unverified attachments: Email-loving cybercriminals are counting on you to download their attachments. Don’t fall for their tricks. Ignore unverified attachments, and don’t click on any links in emails from unknown senders.
-
Use an anti-malware tool: A trustworthy cybersecurity solution will defend you against not just ransomware, but all types of malware and hacking attacks.
-
Keep your software up-to-date: Many malware attacks rely on security holes in outdated software. Make sure to install software patches and updates as soon as they are available.
-
Disable macros in your Microsoft Office programs: Locky’s installation technique kicks in when you enable macros in the attached Word document. Disable macros by default, and then never choose to enable them unless you’re absolutely certain the document is safe.
With Word open, go to File > Options > Trust Center > Trust Center Settings > Macro Settings, then select your desired macro settings.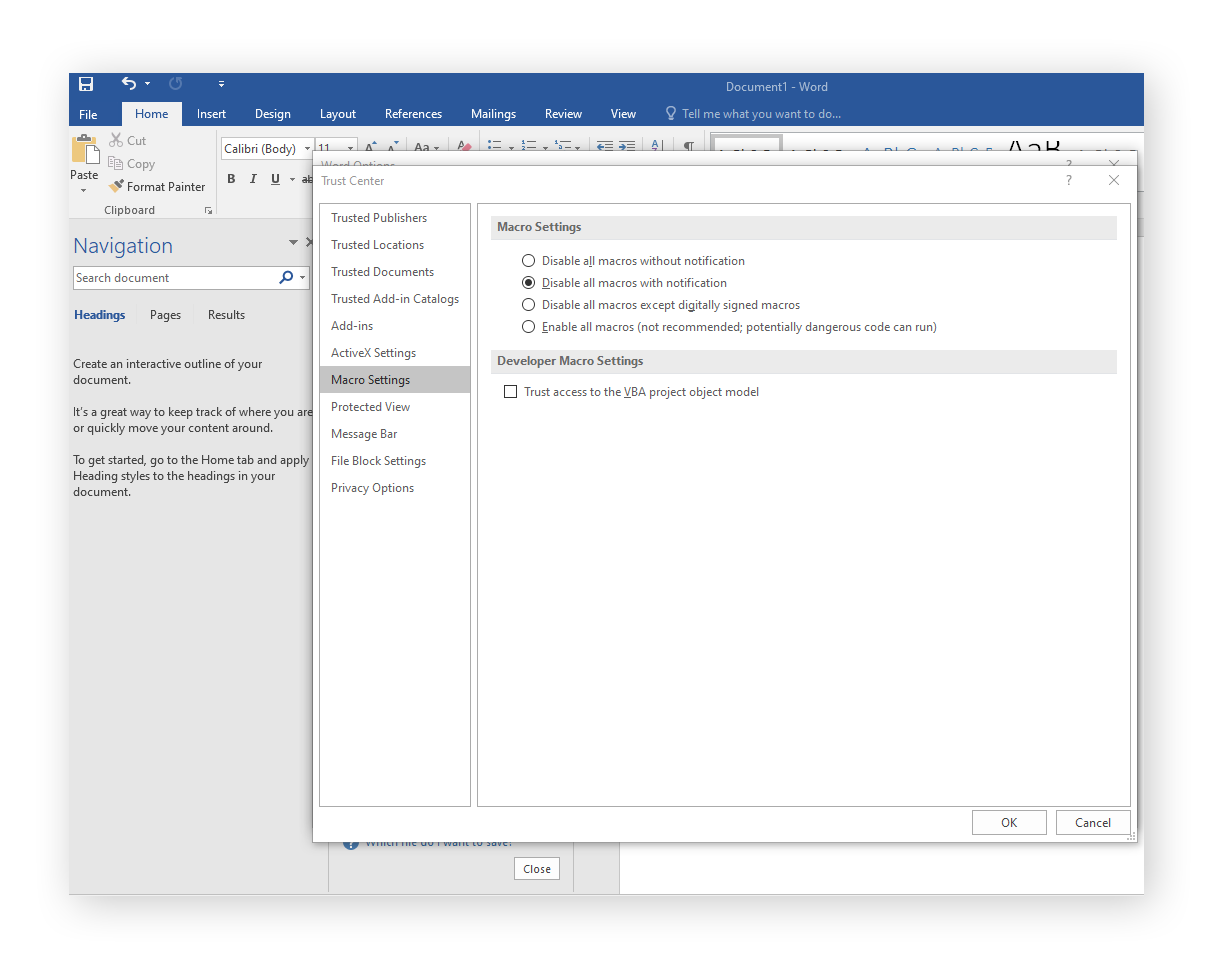
These steps will prevent not only Locky, but also other strains of ransomware like Petya, Cerber, and WannaCry.
Protect yourself with Avast’s anti-ransomware solution
Avast One is your strongest ally in the fight against Locky ransomware. It’ll detect any security weaknesses and out-of-date software so you can get yourself patched up ASAP, while utilizing smart analytics to stay ahead of even the newest threats.
With an advanced AI-based global threat intelligence network, Avast protects over 400 million people around the world. Our cybersecurity solutions will help safeguard your privacy and security on all your devices.

















