Types of identity theft
Identity theft covers a diverse array of crimes, depending on the type of personal data stolen and how the thief uses it. In most data breaches, the information stolen includes full names, social security numbers (or other government-issued IDs), and banking details. As for what constitutes identity theft, most instances of these crimes fall into one of several broad categories.
Financial identity theft
Financial identity theft is the most common and straightforward type of identity theft, because it happens anytime someone uses a victim’s information to fraudulently obtain money. It’s also one of the most damaging types of identity theft, as it represents a direct loss to the victim.
The following examples are just a few ways that financial identity theft can happen. Depending on the information they steal and what they want to do with it, a financial identity thief could:
-
Log into your bank account and transfer money elsewhere.
-
Add their name to your bank account in an “account takeover.”
-
File fraudulent tax paperwork and receive your tax return.
-
Obtain loans or other credit in your name.
-
Make purchases with your credit card or other financial information.
Criminal identity theft
All identity theft is criminal, but criminal identity theft refers to a situation in which someone assumes your identity to avoid legal consequences. Usually, this happens when somebody gives false information to the police when they’re arrested.
Criminal identity thieves may have official government documents fraudulently obtained with their victim’s data, or they may simply have a fake ID. If someone’s out there committing crimes in your name, it can be difficult to convince the police that you’re innocent (and clear your name) — especially if they can’t find the real criminal.
The effects of criminal identity theft can linger for years, since many victims find out about it only by chance, such as when an employer conducts a background check.
Medical identity theft
Medical identity theft happens when someone receives medical treatment in your name. The risks of medical identity theft are especially high in countries with for-profit healthcare systems, like the US — healthcare costs can skyrocket quickly, so the incentives for someone to commit medical identity theft are strong. But even in other countries, medical identity theft is used to help thieves receive treatment or get pharmaceutical drugs they don’t necessarily need.
Then, when the victim goes for medical care themselves, they may find themselves denied treatment, since the thief has already gotten it insead. Victims may also have the thief’s medical history added to their own medical record.
Child identity theft
Child identity theft, perhaps the most insidious type of identity theft, occurs when someone steals and uses a child’s identity to achieve any of the above goals and more. They might use a child’s social security number or other identification to apply for credit, buy property, or obtain official government documents.
Because children typically don’t have any debt or credit, their identities are valuable for anyone looking for a clean source of credit. Sadly, many cases of child identity theft happen within foster care systems, because many different people have access to the children’s information.
Is identity theft a crime?
Absolutely! Like most types of theft, identity theft is an illegal, criminal act. And since identity theft often happens over the internet, it’s a type of cybercrime as well — meaning that these days, identity thieves are cybercriminals.
Identity thieves want your sensitive information so that they can use it to hijack your accounts, buy goods or services, apply for loans and other credit, obtain legal documents in your name, get out of jail, and all sorts of other misdeeds.
How identity theft happens
The internet makes it incredibly easy for identity thieves to get the job done. Whether it’s on social media or on an ecommerce website, we eagerly pump out information about ourselves all the time — our hometowns, jobs, relationships, birthdays, and more are all sitting exposed in the public sphere, waiting to be used against us.
Data breaches
Data breaches, or data leaks, happen when hackers steal sensitive data from a company’s servers or databases. If the hackers can crack the company’s security and access user or customer data — which, depending on the company they target, can include social security numbers, other ID numbers, passwords, addresses, passport numbers, credit card info, and so on — they can sell this data to identity thieves. Data brokers, companies who collect and sell people’s personal information, are frequent targets for data breaches.
Avast Hack Check is a free tool you can use to see if any of your passwords have been exposed in a breach. Try it out!
While big data breaches, such as the 2017 Equifax leak that exposed the data of over 150 million people, sometimes make news headlines, smaller breaches happen every day. Once a hacker exploits a data breach, they’ll usually upload and sell this information on the dark web — and that’s where our identity thieves can get their hands on it.
The dark web
After a data heist, the thieves need to turn that stolen data into profits — this is where the dark web comes in. The dark web is a part of the internet that you won’t find in your everyday Google searches, because you need special software, such as the Tor Browser, to access it. And you need to know where you’re going, because search engines don’t index the dark web.
But if you’re in the know, as many identity thieves are, you can find reams of stolen data for sale. And this is where Avast BreachGuard comes in — we scan the dark web 24/7 for any traces of your data, and if we find any, we’ll alert you ASAP. That way, you can take action to protect yourself before identity thieves have a chance to buy your data and use it against you.
Social media
You know how many websites ask you to set security questions that you can answer when you forget your password? Conveniently for hackers, lots of these answers line up easily with our social media content. Which elementary school did you go to? If a would-be identity thief knows where you grew up, this answer is a piece of cake — if they can get your questions right, then they can walk straight into your account.
Check your privacy settings on Facebook, Instagram, and any other social media platforms you use, and consider making your accounts more private.
Phishing and pharming attacks
Identity thieves can also use phishing and pharming attacks to fool you into handing over sensitive personal information. Phishing attacks involve luring a victim with bait, like a sneaky email that appears to come from a trusted contact, or with messages from a spoofed social media account. If you reply, you risk disclosing the info that the attacker needs to steal your identity.
Pharming is similar to phishing but on a much wider scale. Instead of using phishing bait, pharming attacks stealthily redirect victims to fake websites designed to look like legitimate sites you trust. Once there, if you attempt to log in or conduct other business, you risk giving your personal data to the attacker.
Since both phishing and pharming attacks rely on deception and social engineering tricks, always practice smart email and website safety habits.
Malware
Malware, or malicious software, is a favored tool for many cybercriminals, identity and data thieves included. Certain types of malware are particularly well-suited for the job — like spyware, which can secretly record your online behavior and collect your data. With spyware, you won’t even know that a hacker has infected your computer or phone to stealthily vacuum up all your sensitive personal data.
Avast One protects you with 24/7 malware detection, blocking, and removal. Any malware already on your computer will be immediately removed, and you’ll be safe against future attacks. And should you come across any phishing emails, the built-in Email Shield and Web Shield will detect and block the malicious attachments and links they use to try to fool you.
Avast One is also packed with an assortment of privacy tools to make sure your personal data remains private.
Email hacking
If an identity thief obtains your email password, they can comb through your emails to collect all sorts of information. They can even pose as you and email other people to collect even more information about you and your contacts.
Identity thieves usually buy passwords on the dark web from those who’ve already stolen them. Then, acting as email hackers, they can use malware, phishing, and even various password cracking tools to gain access to your account.
Protect your email account with a strong and unique password that uses a mix of letters, numbers, and symbols (or generate a random password), and update it frequently to keep hackers guessing. Always log out after checking your email on any computer you don’t own. And use a strong password manager to keep track of all your passwords.
Wi-Fi hacking
We talk a lot about being careful on unsecured public Wi-Fi, and here’s why: Anyone with a little hacking know-how and access to the right tools can park their computer on a public Wi-Fi network and spy on everyone else. For a data thief, public Wi-Fi is an all-you-can-eat buffet, and they’re back for their fifth plate.
If your home Wi-Fi router isn’t properly protected with a strong password, hackers can easily gain access to your router. With the ability to control your router, a hacker can redirect your traffic to pharming websites or install malware, like sniffers that collect your data.
Protect yourself on unsecured Wi-Fi with a VPN, which encrypts all your internet traffic, even on unsafe networks. Using a reliable VPN — like Avast SecureLine VPN — is a must any time you’re using public Wi-Fi.


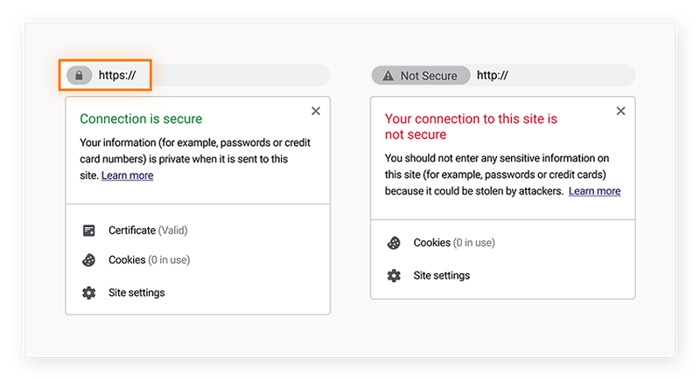 The website on the left has HTTPS encryption and is secure; the site on the right does not.
The website on the left has HTTPS encryption and is secure; the site on the right does not.


